Veracrypt 1 24 update 2
Author: m | 2025-04-24

VeraCrypt 1.25 rc 1 - Download; VeraCrypt 1.24 update 7 - ; VeraCrypt 1.24 - ; VeraCrypt 1.23 hotfix 2 / 1.24 beta 5 - ; VeraCrypt 1.23 hotfix 2 /
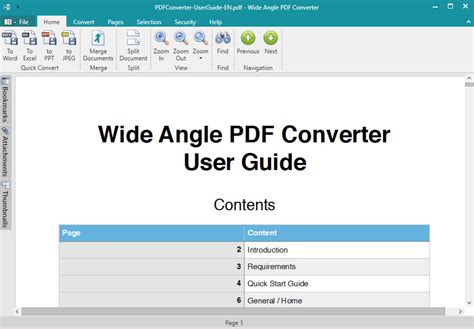
VeraCrypt 1.24 Update 2
How to Install HandBrake on Ubuntu and Other Linux Distros How to Install VeraCrypt on Ubuntu 24.04, 22.04, or 20.04Step 1: Update Your System Start by updating your package list and upgrading any existing packages to ensure that your system is up to date. Open a terminal and run:Step 2: Download VeraCrypt VeraCrypt is not available in the default Ubuntu repositories, so you’ll need to download it from the official website.Step 3: Extract the Downloaded Package Once the download is complete, you need to extract the .tar.bz2 file:Step 4: Install VeraCrypt Navigate to the extracted directory and run the installation script:Step 5: Launch VeraCrypt After the installation is complete, you can launch VeraCrypt from your applications menu or by running the following command in the terminal:Step 6: Using VeraCrypt Creating an Encrypted VolumeStep 7: Uninstalling VeraCrypt (if needed) If you ever need to uninstall VeraCrypt, you can do so using the following command:ConclusionHow to Install VeraCrypt on Ubuntu 24.04, 22.04, or 20.04VeraCrypt is a free and open-source disk encryption software that provides a robust solution for securing your data. It allows you to create a virtual encrypted disk within a file or encrypt an entire partition. This guide will walk you through the installation of VeraCrypt on Ubuntu 24.04, 22.04, or 20.04.PrerequisitesBefore you begin, ensure that you have the following:A computer running Ubuntu 24.04, 22.04, or 20.04.An active internet connection.Administrative (sudo) access.Step 1: Update Your SystemStart by updating your package list and upgrading any existing packages to ensure that your system is up to date. Open a terminal and run:sudo apt updatesudo apt upgrade -yStep 2: Download VeraCryptVeraCrypt is not available in the default Ubuntu repositories, so you’ll need to download it from the official website.Go to the VeraCrypt download page: VeraCrypt Download PageSelect the appropriate version for Linux. Look for the latest .tar.bz2 package for your architecture (32-bit or 64-bit).Download the package using wget:Replace VERSION with the actual version number you want to download:wget 3: Extract the Downloaded PackageOnce the download is complete, you need to extract the .tar.bz2 file:tar -xvjf VeraCrypt*Setup.tar.bz2This command will create a directory with the
Update to VeraCrypt 1.19 1 - GitHub
Idrix, the company behind the encryption software VeraCrypt released VeraCrypt 1.23 for all supported operating systems. VeraCrypt does not support automatic updates; users and administrators need to download the new version from the official website or through third-party services if available. Windows users may download a portable version or a version that is installed. The setup version will upgrade any installed copy of VeraCrypt on the system. Please note that it is required to restart the system as the boot driver is updated in the process. VeraCrypt 1.23 comes more than five months after the release of VeraCrypt 1.22. VeraCrypt 1.23 VeraCrypt 1.23 comes with operating system specific changes for Windows, Mac OS X and Linux. The Windows version of VeraCrypt received quite a few important changes and new features. Probably the biggest feature addition of VeraCrypt 1.23 is that VeraCrypt users don't need to decrypt the system partition anymore to upgrade to a new version of Windows 10. Starting with VeraCrypt 1.23, VeraCrypt is compatible with the upgrading process so that upgrading should be less time-consuming and more straightforward for systems with a VeryCrypt encrypted system partition. Decryption of the system partition is a time-consuming process. The decryption process depends largely on the size and speed of the drive. While having to decrypt the partition was bad enough, it was necessary to encrypt the partition again once the upgrade completed. The next Windows 10 feature update, called the October 2018 Update, will be released at the end of this month or the beginning of the coming month and it will be the first major version that would have required the decryption of the VeraCrypt encrypted system partition. Another, equally important change is support for default EFI SecureBoot configurations for regular versions of Windows and LTSB versions (Long Term Servicing Branch). Idrix added a new option to the performance and driver settings: "Allow Windows Disk Defragmenter to defragment non system partition/drive" allows the built-in disk defragmentation tool to work with VeraCrypt encrypted disks. Windows users benefit from several other changes: protection against some forms of tampering thanks to internal verification checks and Secure Desktop improvements. The list of changes of the Mac and Linux versions of VeraCrypt is much shorter: Support for pasting password values on Mac OS X. New Checkbox to force the use of the embedded backup header during mount (Linux and Mac). If the backing up of the header fails, try to back up the embedded header instead automatically (Linux and Mac). New benchmark UI for Hash and PKCS-5 PRF algorithms (Linux and Mac). Hidden volume protection limitation lifted for disks with sector sizes larger than 512 bytes (Linux) Closing Words and verdict VeraCrypt 1.23 is anVeraCrypt 1.24 Update 2 Download - FileHorse
Skip to content Navigation Menu GitHub Copilot Write better code with AI Security Find and fix vulnerabilities Actions Automate any workflow Codespaces Instant dev environments Issues Plan and track work Code Review Manage code changes Discussions Collaborate outside of code Code Search Find more, search less Explore Learning Pathways Events & Webinars Ebooks & Whitepapers Customer Stories Partners Executive Insights GitHub Sponsors Fund open source developers The ReadME Project GitHub community articles Enterprise platform AI-powered developer platform Pricing Provide feedback Saved searches Use saved searches to filter your results more quickly //voltron/issues_fragments/issue_layout;ref_cta:Sign up;ref_loc:header logged out"}"> Sign up Notifications You must be signed in to change notification settings Fork 990 Star 7.4k Descriptioni'm on windows 10 , veracrypt 1.25.4 , using disk encryption , i noticed a new update was released (1.25.7), the .exe file said it can't update it becasue i originally used msi installer (used it because it seemed to be suggested for newer os) , when trying to update using msi installer i get : "veracrypt msi installation is currently not compatible with windows system encryption"so how can i update veracrypt ?. VeraCrypt 1.25 rc 1 - Download; VeraCrypt 1.24 update 7 - ; VeraCrypt 1.24 - ; VeraCrypt 1.23 hotfix 2 / 1.24 beta 5 - ; VeraCrypt 1.23 hotfix 2 / VeraCrypt 1.25 rc 1 - Download; VeraCrypt 1.24 update 7 - ; VeraCrypt 1.24 - ; VeraCrypt 1.23 hotfix 2 / 1.24 beta 5 - ; VeraCrypt 1.23 hotfix 2 / 1.24 beta 3 - ; VeraCrypt 1.23 hotfix 2 / 1.24 beta 1 - ; VeraCrypt 1.23 hotfix 2 / 1.24 beta 0 - ; VeraCrypt 1.23 - 13/09Downloading VeraCrypt 1.24 Update 2 from FileHorse.com
Elcomsoft Forensic Disk Decryptor Crack offers all available methods for gaining access to information stored in encrypted BitLocker, FileVault 2, PGP, TrueCrypt, and VeraCrypt disks and volumes. The toolkit allows using the volume’s plain-text password, escrow or recovery keys, as well as the binary keys extracted from the computer’s memory image or hibernation file. FileVault 2 recovery keys can be extracted from iCloud with Elcomsoft Phone Breaker, while BitLocker recovery keys are available in Active Directory or in the user’s Microsoft Account.Elcomsoft Forensic Disk Decryptor Full Version can automatically decrypt the entire content of the encrypted container, providing investigators with full, unrestricted access to all information stored on encrypted volumes.Elcomsoft Forensic Disk Decryptor Key Features:VeraCrypt EncryptionVeraCrypt is the most popular successor to open-source disk encryption tool TrueCrypt. Compared to the original, VeraCrypt supposes a wider range of encryption methods and hash algorithms. In this update,Elcomsoft Forensic Disk Decryptor receives full support for VeraCrypt volumes, enabling experts extracting hash data from VeraCrypt containers to launch brute-force or smart dictionary attacks with Distributed Password Recovery.Elcomsoft Forensic Disk Decryptor License KeyWhat’s New In Elcomsoft Forensic Disk Decryptor Crack?added support for APFS partitions with FileVault2added support for VeraCrypt (generating files for further password recovery)added support for GUID partitionsimproved support for encrypted HFS+ partitionsimproved UI; disk letters are now availableimproved PGP WDE supportHow To Crack, patch & activate Elcomsoft Forensic Disk Decryptor Full Version for free?Download latest version from below linksInstall program & do not runCopy Crack And Replace To Install DirectoryDone! Enjoy Elcomsoft Forensic Disk Decryptor Full Cracked 😉Elcomsoft Forensic Disk Decryptor 2.11.751 Crack Download Links:Download NowDe 25 1 2 24
Installation files.Step 4: Install VeraCryptNavigate to the extracted directory and run the installation script:cd VeraCrypt*sudo ./veracrypt-*-setup-gui.shFollow the prompts in the GUI installer to complete the installation. You may be asked to accept the license agreement and choose installation options.Step 5: Launch VeraCryptAfter the installation is complete, you can launch VeraCrypt from your applications menu or by running the following command in the terminal:veracryptStep 6: Using VeraCryptCreating an Encrypted VolumeOpen VeraCrypt.Click on “Create Volume.”Choose whether to create a standard or hidden VeraCrypt volume, then click “Next.”Follow the prompts to specify the location, encryption options, and volume size.Set a strong password for your encrypted volume.Mounting an Encrypted VolumeTo mount an existing encrypted volume:Open VeraCrypt.Select a drive letter (slot) from the list.Click on “Select File” and browse to your encrypted volume file.Click “Mount” and enter your password when prompted.The encrypted volume will now be accessible as a mounted drive in your file manager.Dismounting a VolumeWhen you’re finished using the encrypted volume, it’s essential to dismount it:Select the mounted volume in VeraCrypt.Click “Dismount.”Step 7: Uninstalling VeraCrypt (if needed)If you ever need to uninstall VeraCrypt, you can do so using the following command:sudo apt remove veracryptConclusionYou have successfully installed VeraCrypt on your Ubuntu system. With VeraCrypt, you can ensure that your sensitive data remains secure through strong encryption methods. Regularly update VeraCrypt to benefit from the latest security features and enhancements.For more information on using VeraCrypt, consult the official VeraCrypt documentation. Post Views: 6052 Samuel 1:24 - Bible.com
You are receiving this mail as a port that you maintainis failing to build on the FreeBSD package build server.Please investigate the failure and submit a PR to fixbuild.Maintainer: [email protected] committer: [email protected]: $FreeBSD: branches/2019Q3/security/veracrypt/Makefile 493853 2019-02-25 12:47:20Z bapt $Log URL: URL: Building security/veracryptbuild started at Sun Sep 15 01:49:11 UTC 2019port directory: /usr/ports/security/veracryptpackage name: veracrypt-1.23_2building for: FreeBSD 120armv7-quarterly-job-06 12.0-RELEASE-p10 FreeBSD 12.0-RELEASE-p10 1200086 armmaintained by: [email protected] ident: $FreeBSD: branches/2019Q3/security/veracrypt/Makefile 493853 2019-02-25 12:47:20Z bapt $Poudriere version: 3.2.8-5-gc81843e5Host OSVERSION: 1300031Jail OSVERSION: 1200086Job Id: 06---Begin Environment---SHELL=/bin/cshUNAME_p=armv7UNAME_m=armABI_FILE=/usr/lib/crt1.oOSVERSION=1200086UNAME_v=FreeBSD 12.0-RELEASE-p10 1200086UNAME_r=12.0-RELEASE-p10BLOCKSIZE=KMAIL=/var/mail/rootSTATUS=1HOME=/rootPATH=/sbin:/bin:/usr/sbin:/usr/bin:/usr/local/sbin:/usr/local/bin:/root/binLOCALBASE=/usr/localQEMU_EMULATING=1USER=rootLIBEXECPREFIX=/usr/local/libexec/poudrierePOUDRIERE_VERSION=3.2.8-5-gc81843e5MASTERMNT=/usr/local/poudriere/data/.m/120armv7-quarterly/refPOUDRIERE_BUILD_TYPE=bulkPACKAGE_BUILDING=yesSAVED_TERM=PWD=/usr/local/poudriere/data/.m/120armv7-quarterly/ref/.p/poolP_PORTS_FEATURES=FLAVORS SELECTED_OPTIONSMASTERNAME=120armv7-quarterlySCRIPTPREFIX=/usr/local/share/poudriereOLDPWD=/usr/local/poudriere/data/.m/120armv7-quarterly/ref/.pSCRIPTPATH=/usr/local/share/poudriere/bulk.shPOUDRIEREPATH=/usr/local/bin/poudriere---End Environment------Begin Poudriere Port Flags/Env---PORT_FLAGS=PKGENV=FLAVOR=DEPENDS_ARGS=MAKE_ARGS=---End Poudriere Port Flags/Env------Begin OPTIONS List---===> The following configuration options are available for veracrypt-1.23_2: DOCS=on: Build and/or install documentation===> Use 'make config' to modify these settings---End OPTIONS [email protected] MAINTAINER----CONFIGURE_ARGS----End CONFIGURE_ARGS----CONFIGURE_ENV--MAKE=gmake PKG_CONFIG=pkgconf XDG_DATA_HOME=/wrkdirs/usr/ports/security/veracrypt/work XDG_CONFIG_HOME=/wrkdirs/usr/ports/security/veracrypt/work HOME=/wrkdirs/usr/ports/security/veracrypt/work TMPDIR="/tmp" PATH=/wrkdirs/usr/ports/security/veracrypt/work/.bin:/sbin:/bin:/usr/sbin:/usr/bin:/usr/local/sbin:/usr/local/bin:/root/bin SHELL=/bin/sh CONFIG_SHELL=/bin/sh WX_CONFIG=/usr/local/bin/wxgtk3u-3.0-config--End CONFIGURE_ENV----MAKE_ENV--XDG_DATA_HOME=/wrkdirs/usr/ports/security/veracrypt/work XDG_CONFIG_HOME=/wrkdirs/usr/ports/security/veracrypt/work HOME=/wrkdirs/usr/ports/security/veracrypt/work TMPDIR="/tmp" PATH=/wrkdirs/usr/ports/security/veracrypt/work/.bin:/sbin:/bin:/usr/sbin:/usr/bin:/usr/local/sbin:/usr/local/bin:/root/bin NO_PIE=yes MK_DEBUG_FILES=no MK_KERNEL_SYMBOLS=no SHELL=/bin/sh NO_LINT=YES WX_CONFIG=/usr/local/bin/wxgtk3u-3.0-config PREFIX=/usr/local LOCALBASE=/usr/local CC="/nxb-bin/usr/bin/cc" CFLAGS="-O2 -pipe -DLIBICONV_PLUG -fstack-protector-strong -fno-strict-aliasing " CPP="/nxb-bin/usr/bin/cpp" CPPFLAGS="-DLIBICONV_PLUG" LDFLAGS=" -fstack-protector-strong " LIBS="" CXX="/nxb-bin/usr/bin/c++" CXXFLAGS="-O2 -pipe -DLIBICONV_PLUG -fstack-protector-strong -fno-strict-aliasing -DLIBICONV_PLUG " MANPREFIX="/usr/local" BSD_INSTALL_PROGRAM="install -s -m 555" BSD_INSTALL_LIB="install -s -m 0644" BSD_INSTALL_SCRIPT="install -m 555" BSD_INSTALL_DATA="install -m 0644" BSD_INSTALL_MAN ="install -m 444"--End MAKE_ENV----PLIST_SUB--PORTDOCS="" OSREL=12.0 PREFIX=%D LOCALBASE=/usr/local RESETPREFIX=/usr/local LIB32DIR=lib DOCSDIR="share/doc/veracrypt" EXAMPLESDIR="share/examples/veracrypt" DATADIR="share/veracrypt" WWWDIR="www/veracrypt" ETCDIR="etc/veracrypt"--End PLIST_SUB----SUB_LIST--PREFIX=/usr/local LOCALBASE=/usr/local DATADIR=/usr/local/share/veracrypt DOCSDIR=/usr/local/share/doc/veracrypt EXAMPLESDIR=/usr/local/share/examples/veracrypt WWWDIR=/usr/local/www/veracrypt ETCDIR=/usr/local/etc/veracrypt--End SUB_LIST-----Begin make.conf---.sinclude "/etc/make.nxb.conf"USE_PACKAGE_DEPENDS=yesBATCH=yesWRKDIRPREFIX=/wrkdirsPORTSDIR=/usr/portsPACKAGES=/packagesDISTDIR=/distfilesPACKAGE_BUILDING=yesPACKAGE_BUILDING_FLAVORS=yesMACHINE=armMACHINE_ARCH=armv7ARCH=${MACHINE_ARCH}#### /usr/local/etc/poudriere.d/make.conf ##### XXX: We really need this but cannot use it while 'make checksum' does not# try the next mirror on checksum failure. It currently retries the same# failed mirror and then fails rather then trying another. It *does*# try the next if the size is mismatched though.#MASTER_SITE_FREEBSD=yes# Build ALLOW_MAKE_JOBS_PACKAGES with 2 jobsMAKE_JOBS_NUMBER=2# stable/10 includes src.conf too late but make.conf is in sys.mk.if ${.CURDIR:M/poudriere/jails/10*/usr/src/usr.bin/xlint*}# Disable build of llib now that head no longer has lint(1)LINT= true.endif#### /usr/ports/Mk/Scripts/ports_env.sh ####_CCVERSION_9d218390=FreeBSD clang version 6.0.1 (tags/RELEASE_601/final 335540) (based on LLVM 6.0.1) Target: armv7-unknown-freebsd12.0-gnueabihf Thread model: posix InstalledDir: /nxb-bin/usr/bin_ALTCCVERSION_9d218390=none_CXXINTERNAL_9c45a5b1=FreeBSD clang version 6.0.1 (tags/RELEASE_601/final 335540) (based on LLVM 6.0.1) Target: armv7-unknown-freebsd12.0-gnueabihf Thread model: posix InstalledDir: /nxb-bin/usr/bin "/nxb-bin/usr/bin/ld" "--eh-frame-hdr" "-dynamic-linker" "/libexec/ld-elf.so.1" "--hash-style=both" "--enable-new-dtags" "-o" "a.out" "/usr/lib/crt1.o" "/usr/lib/crti.o" "/usr/lib/crtbegin.o" "-L/usr/lib" "/dev/null" "-lc++" "-lm" "-lgcc" "--as-needed" "-lgcc_s" "--no-as-needed" "-lc" "-lgcc" "--as-needed" "-lgcc_s" "--no-as-needed" "/usr/lib/crtend.o" "/usr/lib/crtn.o"CC_OUTPUT_9d218390_58173849=yesCC_OUTPUT_9d218390_9bdba57c=yesCC_OUTPUT_9d218390_6a4fe7f5=yesCC_OUTPUT_9d218390_6bcac02b=yesCC_OUTPUT_9d218390_67d20829=yesCC_OUTPUT_9d218390_bfa62e83=yesCC_OUTPUT_9d218390_f0b4d593=yesCC_OUTPUT_9d218390_308abb44=yesCC_OUTPUT_9d218390_f00456e5=yesCC_OUTPUT_9d218390_65ad290d=yesCC_OUTPUT_9d218390_f2776b26=yesCC_OUTPUT_9d218390_b2657cc3=yesCC_OUTPUT_9d218390_380987f7=yesCC_OUTPUT_9d218390_160933ec=yesCC_OUTPUT_9d218390_fb62803b=yes_OBJC_CCVERSION_9d218390=FreeBSD clang version 6.0.1 (tags/RELEASE_601/final 335540) (based on LLVM 6.0.1) Target: armv7-unknown-freebsd12.0-gnueabihf Thread model: posix InstalledDir: /nxb-bin/usr/bin_OBJC_ALTCCVERSION_9d218390=noneARCH=armv7OPSYS=FreeBSD_OSRELEASE=12.0-RELEASE-p10OSREL=12.0OSVERSION=1200086PYTHONBASE=/usr/localCONFIGURE_MAX_CMD_LEN=262144HAVE_PORTS_ENV=1#### Misc Poudriere ####GID=0UID=0DISABLE_MAKE_JOBS=poudriere---End make.conf------Begin make.nxb.conf---CC=/nxb-bin/usr/bin/ccCPP=/nxb-bin/usr/bin/cppCXX=/nxb-bin/usr/bin/c++AS=/nxb-bin/usr/bin/asNM=/nxb-bin/usr/bin/nmLD=/nxb-bin/usr/bin/ldOBJCOPY=/nxb-bin/usr/bin/objcopySIZE=/nxb-bin/usr/bin/sizeSTRIPBIN=/nxb-bin/usr/bin/stripSED=/nxb-bin/usr/bin/sedRANLIB=/nxb-bin/usr/bin/ranlibYACC=/nxb-bin/usr/bin/yaccMAKE=/nxb-bin/usr/bin/makeSTRINGS=/nxb-bin/usr/bin/stringsAWK=/nxb-bin/usr/bin/awkFLEX=/nxb-bin/usr/bin/flex---End make.nxb.conf-----Resource limits--cpu time (seconds, -t) unlimitedfile size (512-blocks, -f) unlimiteddata seg size (kbytes, -d) 33554432stack size (kbytes, -s) 524288core file size (512-blocks, -c) unlimitedmax memory size (kbytes, -m) unlimitedlocked memory (kbytes, -l) unlimitedmax user processes (-u) 89999open files (-n) 1024virtual mem size (kbytes, -v) unlimitedswap limit (kbytes, -w) unlimitedsocket buffer size (bytes, -b) unlimitedpseudo-terminals (-p) unlimitedkqueues (-k) unlimitedumtx shared locks (-o) unlimited--End resource limits--====================================================================================================================================================================================> veracrypt-1.23_2 depends on file: /usr/local/sbin/pkg - not found===> Installing existing package /packages/All/pkg-1.11.1.txz[120armv7-quarterly-job-06] Installing pkg-1.11.1...[120armv7-quarterly-job-06] Extracting pkg-1.11.1: .......... done===> veracrypt-1.23_2 depends on file: /usr/local/sbin/pkg - found===> Returning to build of veracrypt-1.23_2===============================================================================================================================================================================================================================================================> Fetching all distfiles required by veracrypt-1.23_2 for building=================================================================================================================================> Fetching all distfiles required by veracrypt-1.23_2 for building=> SHA256 Checksum OK for VeraCrypt_1.23_Source.tar.bz2.============================================================================================================================================================================================================================================================/usr/local/include/wx-3.0/wx/gtk/window.h:92:17: note: hidden overloaded virtual function 'wxWindow::GetCharWidth' declared here: different number of parameters (0 vs 1) virtual int GetCharWidth() const; ^1 warning generated.Compiling MountOptionsDialog.cppIn file included from Forms/MountOptionsDialog.cpp:15:In. VeraCrypt 1.25 rc 1 - Download; VeraCrypt 1.24 update 7 - ; VeraCrypt 1.24 - ; VeraCrypt 1.23 hotfix 2 / 1.24 beta 5 - ; VeraCrypt 1.23 hotfix 2 / VeraCrypt 1.25 rc 1 - Download; VeraCrypt 1.24 update 7 - ; VeraCrypt 1.24 - ; VeraCrypt 1.23 hotfix 2 / 1.24 beta 5 - ; VeraCrypt 1.23 hotfix 2 / 1.24 beta 3 - ; VeraCrypt 1.23 hotfix 2 / 1.24 beta 1 - ; VeraCrypt 1.23 hotfix 2 / 1.24 beta 0 - ; VeraCrypt 1.23 - 13/09Comments
How to Install HandBrake on Ubuntu and Other Linux Distros How to Install VeraCrypt on Ubuntu 24.04, 22.04, or 20.04Step 1: Update Your System Start by updating your package list and upgrading any existing packages to ensure that your system is up to date. Open a terminal and run:Step 2: Download VeraCrypt VeraCrypt is not available in the default Ubuntu repositories, so you’ll need to download it from the official website.Step 3: Extract the Downloaded Package Once the download is complete, you need to extract the .tar.bz2 file:Step 4: Install VeraCrypt Navigate to the extracted directory and run the installation script:Step 5: Launch VeraCrypt After the installation is complete, you can launch VeraCrypt from your applications menu or by running the following command in the terminal:Step 6: Using VeraCrypt Creating an Encrypted VolumeStep 7: Uninstalling VeraCrypt (if needed) If you ever need to uninstall VeraCrypt, you can do so using the following command:ConclusionHow to Install VeraCrypt on Ubuntu 24.04, 22.04, or 20.04VeraCrypt is a free and open-source disk encryption software that provides a robust solution for securing your data. It allows you to create a virtual encrypted disk within a file or encrypt an entire partition. This guide will walk you through the installation of VeraCrypt on Ubuntu 24.04, 22.04, or 20.04.PrerequisitesBefore you begin, ensure that you have the following:A computer running Ubuntu 24.04, 22.04, or 20.04.An active internet connection.Administrative (sudo) access.Step 1: Update Your SystemStart by updating your package list and upgrading any existing packages to ensure that your system is up to date. Open a terminal and run:sudo apt updatesudo apt upgrade -yStep 2: Download VeraCryptVeraCrypt is not available in the default Ubuntu repositories, so you’ll need to download it from the official website.Go to the VeraCrypt download page: VeraCrypt Download PageSelect the appropriate version for Linux. Look for the latest .tar.bz2 package for your architecture (32-bit or 64-bit).Download the package using wget:Replace VERSION with the actual version number you want to download:wget 3: Extract the Downloaded PackageOnce the download is complete, you need to extract the .tar.bz2 file:tar -xvjf VeraCrypt*Setup.tar.bz2This command will create a directory with the
2025-04-19Idrix, the company behind the encryption software VeraCrypt released VeraCrypt 1.23 for all supported operating systems. VeraCrypt does not support automatic updates; users and administrators need to download the new version from the official website or through third-party services if available. Windows users may download a portable version or a version that is installed. The setup version will upgrade any installed copy of VeraCrypt on the system. Please note that it is required to restart the system as the boot driver is updated in the process. VeraCrypt 1.23 comes more than five months after the release of VeraCrypt 1.22. VeraCrypt 1.23 VeraCrypt 1.23 comes with operating system specific changes for Windows, Mac OS X and Linux. The Windows version of VeraCrypt received quite a few important changes and new features. Probably the biggest feature addition of VeraCrypt 1.23 is that VeraCrypt users don't need to decrypt the system partition anymore to upgrade to a new version of Windows 10. Starting with VeraCrypt 1.23, VeraCrypt is compatible with the upgrading process so that upgrading should be less time-consuming and more straightforward for systems with a VeryCrypt encrypted system partition. Decryption of the system partition is a time-consuming process. The decryption process depends largely on the size and speed of the drive. While having to decrypt the partition was bad enough, it was necessary to encrypt the partition again once the upgrade completed. The next Windows 10 feature update, called the October 2018 Update, will be released at the end of this month or the beginning of the coming month and it will be the first major version that would have required the decryption of the VeraCrypt encrypted system partition. Another, equally important change is support for default EFI SecureBoot configurations for regular versions of Windows and LTSB versions (Long Term Servicing Branch). Idrix added a new option to the performance and driver settings: "Allow Windows Disk Defragmenter to defragment non system partition/drive" allows the built-in disk defragmentation tool to work with VeraCrypt encrypted disks. Windows users benefit from several other changes: protection against some forms of tampering thanks to internal verification checks and Secure Desktop improvements. The list of changes of the Mac and Linux versions of VeraCrypt is much shorter: Support for pasting password values on Mac OS X. New Checkbox to force the use of the embedded backup header during mount (Linux and Mac). If the backing up of the header fails, try to back up the embedded header instead automatically (Linux and Mac). New benchmark UI for Hash and PKCS-5 PRF algorithms (Linux and Mac). Hidden volume protection limitation lifted for disks with sector sizes larger than 512 bytes (Linux) Closing Words and verdict VeraCrypt 1.23 is an
2025-04-19Elcomsoft Forensic Disk Decryptor Crack offers all available methods for gaining access to information stored in encrypted BitLocker, FileVault 2, PGP, TrueCrypt, and VeraCrypt disks and volumes. The toolkit allows using the volume’s plain-text password, escrow or recovery keys, as well as the binary keys extracted from the computer’s memory image or hibernation file. FileVault 2 recovery keys can be extracted from iCloud with Elcomsoft Phone Breaker, while BitLocker recovery keys are available in Active Directory or in the user’s Microsoft Account.Elcomsoft Forensic Disk Decryptor Full Version can automatically decrypt the entire content of the encrypted container, providing investigators with full, unrestricted access to all information stored on encrypted volumes.Elcomsoft Forensic Disk Decryptor Key Features:VeraCrypt EncryptionVeraCrypt is the most popular successor to open-source disk encryption tool TrueCrypt. Compared to the original, VeraCrypt supposes a wider range of encryption methods and hash algorithms. In this update,Elcomsoft Forensic Disk Decryptor receives full support for VeraCrypt volumes, enabling experts extracting hash data from VeraCrypt containers to launch brute-force or smart dictionary attacks with Distributed Password Recovery.Elcomsoft Forensic Disk Decryptor License KeyWhat’s New In Elcomsoft Forensic Disk Decryptor Crack?added support for APFS partitions with FileVault2added support for VeraCrypt (generating files for further password recovery)added support for GUID partitionsimproved support for encrypted HFS+ partitionsimproved UI; disk letters are now availableimproved PGP WDE supportHow To Crack, patch & activate Elcomsoft Forensic Disk Decryptor Full Version for free?Download latest version from below linksInstall program & do not runCopy Crack And Replace To Install DirectoryDone! Enjoy Elcomsoft Forensic Disk Decryptor Full Cracked 😉Elcomsoft Forensic Disk Decryptor 2.11.751 Crack Download Links:Download Now
2025-04-04Installation files.Step 4: Install VeraCryptNavigate to the extracted directory and run the installation script:cd VeraCrypt*sudo ./veracrypt-*-setup-gui.shFollow the prompts in the GUI installer to complete the installation. You may be asked to accept the license agreement and choose installation options.Step 5: Launch VeraCryptAfter the installation is complete, you can launch VeraCrypt from your applications menu or by running the following command in the terminal:veracryptStep 6: Using VeraCryptCreating an Encrypted VolumeOpen VeraCrypt.Click on “Create Volume.”Choose whether to create a standard or hidden VeraCrypt volume, then click “Next.”Follow the prompts to specify the location, encryption options, and volume size.Set a strong password for your encrypted volume.Mounting an Encrypted VolumeTo mount an existing encrypted volume:Open VeraCrypt.Select a drive letter (slot) from the list.Click on “Select File” and browse to your encrypted volume file.Click “Mount” and enter your password when prompted.The encrypted volume will now be accessible as a mounted drive in your file manager.Dismounting a VolumeWhen you’re finished using the encrypted volume, it’s essential to dismount it:Select the mounted volume in VeraCrypt.Click “Dismount.”Step 7: Uninstalling VeraCrypt (if needed)If you ever need to uninstall VeraCrypt, you can do so using the following command:sudo apt remove veracryptConclusionYou have successfully installed VeraCrypt on your Ubuntu system. With VeraCrypt, you can ensure that your sensitive data remains secure through strong encryption methods. Regularly update VeraCrypt to benefit from the latest security features and enhancements.For more information on using VeraCrypt, consult the official VeraCrypt documentation. Post Views: 605
2025-04-14